In one of my previous posts, I showed how to install Istio on minikube and deploy the sample BookInfo app. A new Istio version is out (0.8.0) with a lot of changes, especially changes on traffic management, which made my steps in the previous post a little obsolete.
In this post, I want to show how to install Istio 0.8.0 on Google Kubernetes Engine (GKE), deploy the sample BookInfo app and show some of the add-ons and traffic routing.
Create Kubernetes cluster
First, we need a Kubernetes cluster to install Istio. On GKE, this is a single command:
gcloud container clusters create hello-istio \\ --cluster-version=1.9.7-gke.1 \\ --zone europe-west1-b \\ --num-nodes 4
A couple of things to note. First, I’m not using the latest cluster-version on GKE (1.10) because Istio 0.8.0 does not work against it (yet). Second, I’m using 4 worker nodes. That’s the recommended number of nodes for BookInfo sample.
Once the cluster is created, we also need to create a clusterrolebinding for Istio to be able to manage the cluster:
kubectl create clusterrolebinding cluster-admin-binding \\ --clusterrole=cluster-admin \\ --user=$(gcloud config get-value core/account)
Download & Setup Istio
Now that we have a cluster, let’s download the latest Istio (0.8.0 as of today):
curl -L [https://git.io/getLatestIstio](https://git.io/getLatestIstio) | ISTIO\_VERSION=0.8.0 sh -
Add Istio’s command line tool istioctl to your PATH. We’ll need it later:
export PATH="$PATH:./istio-0.8.0/bin"
Install Istio
It’s time to install Istio with mutual authentication between sidecars:
kubectl apply -f install/kubernetes/istio-demo-auth.yaml
Once it’s done, you can check that pods are running under istio-system namespace:
kubectl get pods -n istio-system
You’ll realize that in addition to Istio base components (eg. pilot, mixer, ingress, egress), a number of add-ons are also installed (eg. prometheus, servicegraph, grafana). This is different from the previous versions of Istio.
Deploy BookInfo app
Let’s deploy the BookInfo sample app now:
kubectl apply -f <(istioctl kube-inject --debug -f samples/bookinfo/kube/bookinfo.yaml)
And make sure all the pods are running:
kubectl get pods
Deploy BookInfo Gateway
In Istio 0.8.0, traffic management completely changed and one of those changes is that you need to create a gateway for ingress traffic. Let’s go ahead and create a gateway for BookInfo app:
istioctl create -f samples/bookinfo/routing/bookinfo-gateway.yaml
Use BookInfo app
We can finally take a look at the app. We need to find ingress gateway IP and port:
kubectl get svc istio-ingressgateway -n istio-system
To make it easier for us, let’s define a GATEWAY_URL variable:
export INGRESS\_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress\[0\].ip}') export INGRESS\_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports\[?(@.name=="http")\].port}') export GATEWAY\_URL=$INGRESS\_HOST:$INGRESS\_PORT
Let’s see if the app is working. You should get 200 with curl:
curl -o /dev/null -s -w "%{http\_code}\\n" [http://${GATEWAY\_URL}/productpage](http://$%7BGATEWAY_URL%7D/productpage)
You can also open a browser and see the web frontend for product page. At this point, we got the app deployed and managed by a basic installation of Istio.
Next, we’ll take a look at some of the add-ons. Unlike previous versions, add-ons are automatically installed already. Let’s start sending some traffic first:
for i in {1..100}; do curl -o /dev/null -s -w "%{http\_code}\\n" [http://${GATEWAY\_URL}/productpage;](http://$%7BGATEWAY_URL%7D/productpage;) done
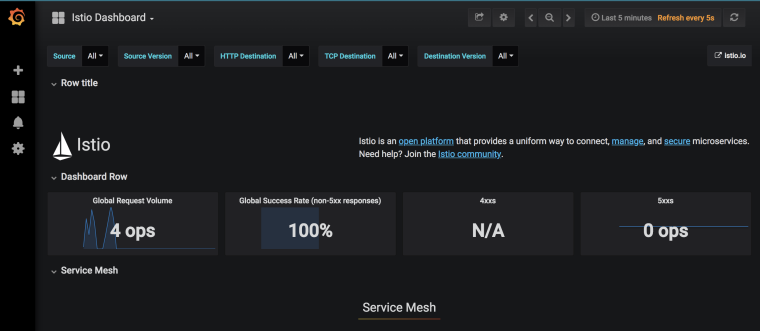
Grafana dashboard
There’s Grafana for dashboarding. Let’s setup port forwarding first:
kubectl -n istio-system port-forward $(kubectl -n istio-system get pod -l app=grafana -o jsonpath='{.items\[0\].metadata.name}') 8080:3000
Navigate to http://localhost:8080 to see the dashboard:
Prometheus metrics
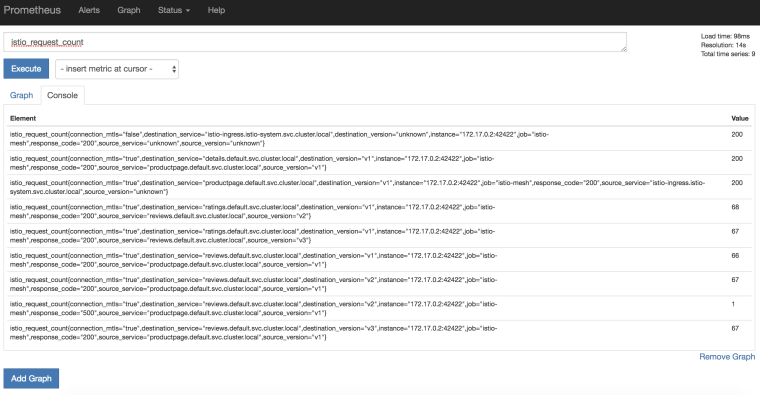
Next, let’s take a look at Prometheus for metrics. Set port forwarding:
kubectl -n istio-system port-forward $(kubectl -n istio-system get pod -l app=prometheus -o jsonpath='{.items\[0\].metadata.name}') 8083:9090
Navigate to http://localhost:8083/graph to see Prometheus:
ServiceGraph
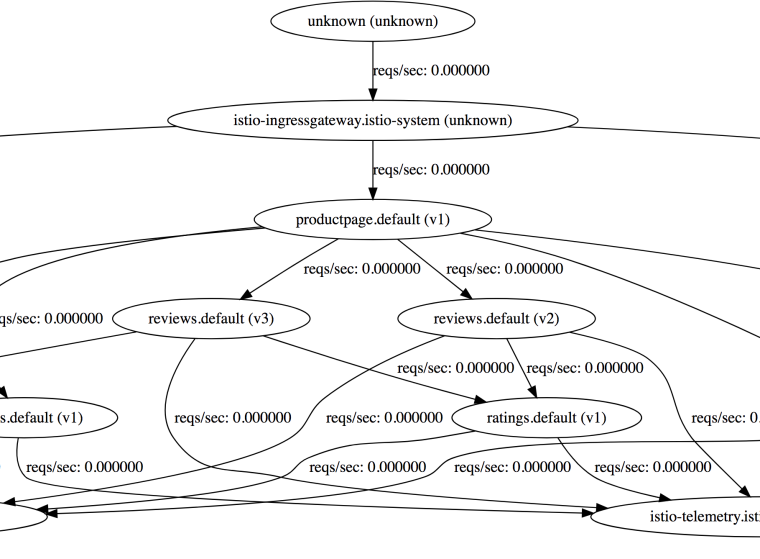
For dependency visualization, we can take a look at ServiceGraph:
kubectl -n istio-system port-forward $(kubectl -n istio-system get pod -l app=servicegraph -o jsonpath='{.items\[0\].metadata.name}') 8082:8088
Navigate to http://localhost:8082/dotviz:
Tracing
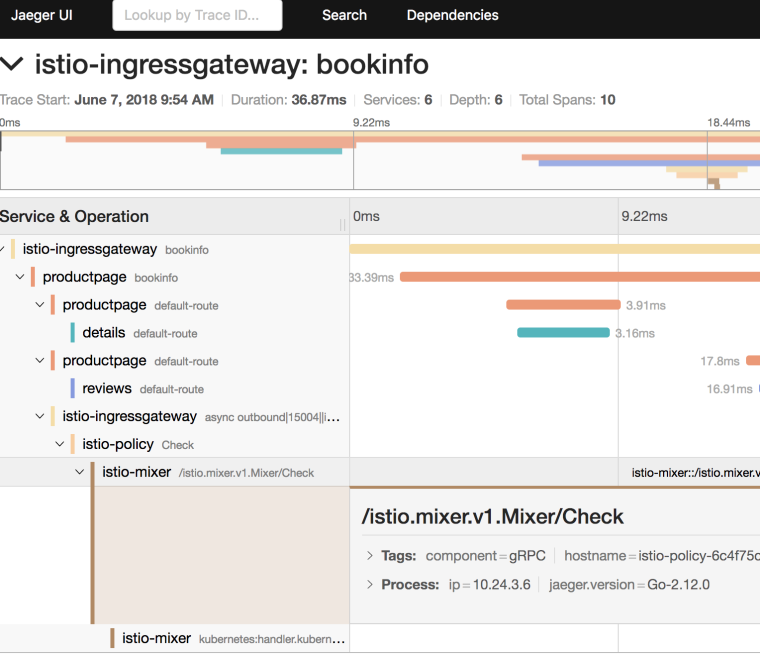
For HTTP tracing, there is Jaegar and Zipkin. Let’s take a look at Jaeger. Setup port forwarding as usual:
kubectl port-forward -n istio-system $(kubectl get pod -n istio-system -l app=jaeger -o jsonpath='{.items\[0\].metadata.name}') 8084:16686
Navigate to http://localhost:8084
Traffic Management
Traffic Management changed dramatically in 0.8.0. You can read more about it here but basically instead of routing rules, we now have VirtualServices and DestinationRules.
You can see the existing VirtualServices and DestinationRules like this:
istioctl get virtualservices -o yaml istioctl get destinationrules -o yaml
When you go to the product page of BookInfo application and do a browser refresh a few times, you will see that the reviews section on the right keeps changing (the stars change color). This is because there are 3 different reviews microservices and everytime, a different microservice is invoked. Let’s pin all microservices to version1:
istioctl create -f samples/bookinfo/routing/route-rule-all-v1-mtls.yaml
This creates VirtualServices and DestinationRules needed to pin all microservices to version1. Now, if you back to the product page and do a browser refresh, nothing changes because reviews microservice is pinned to version1 now.
To pin a specific user (eg. Jason) to a specific version (v2), we can do the following:
istioctl replace -f samples/bookinfo/routing/route-rule-reviews-test-v2.yaml
With this rule, if you login to the product page with username “Jason”, you should see the v2 version of reviews microservice.
To clean up all destination rules, run the following and now we’re back to the beginning with 3 different versions of the microservices:
istioctl delete -f samples/bookinfo/routing/route-rule-all-v1.yaml
Cleanup
This wraps up all the basic functionality of Istio 0.8.0 that I wanted to show on GKE. To cleanup, let’s first delete the BookInfo app:
samples/bookinfo/kube/cleanup.sh
Confirm that BookInfo app is gone:
istioctl get gateway istioctl get virtualservices kubectl get pods
Finally, cleanup Istio:
kubectl delete -f install/kubernetes/istio-demo.yaml
Confirm that Istio is gone:
kubectl get pods -n istio-system